Vol.1 - A WEB of Sharing Trust-responsibility toward a trustless future.
DISCLAIMER
Project Purpose — Please Read Carefully
This document provides an overview of the objectives and utility of emerging Web 3.0 governance concepts, including compliance, regulatory considerations, and the introduction of the open-source initiative Policy of Developments – Access PoD (v1.2).
Purpose and Scope
All contributions, materials, and discussions associated with this project are intended to advance research, dialogue, and development relating to a key missing component of Web 3.0 infrastructure:
a decentralized notification and policy reporting protocol.
This capability is considered foundational to the long-term potential of Web 3.0 systems, particularly where transparency, accountability, and policy signaling are required across decentralized environments.
Participation and feedback support the exploration of how trust, responsibility, and policy signaling may be structured in such systems. Contributions do not imply endorsement, certification, or regulatory approval.
Jurisdiction and Authority
The organization, distributors, and any affiliated contributors operate within applicable legal and jurisdictional frameworks, but do not act on behalf of, represent, or exercise authority as:
a government entity,
a regulatory body,
an administrative agency, or
any nation, state, or public authority.
At this stage, the initiative functions solely as an independent, arms-length third party, contributing research, technical exploration, and conceptual models related to compliance and policy signaling. It does not administer, enforce, or adjudicate regulatory or administrative law.
Design and Configuration Notice
All designs, frameworks, and examples presented are illustrative and non-prescriptive.
References to operational factors, configurations, or sequencing (including examples involving six operational factors) are provided for conceptual demonstration only. These elements may be adapted, reconfigured, or repurposed to suit different policy development contexts or notification models.
Nothing in this material should be interpreted as a fixed standard, mandatory implementation, or legally binding configuration.
————————————————————
Trust is one of the most important aspects everyone values, especially when it comes to online interactions. Without trust, many people will not interact with others online or even use websites for transactions because they feel unsafe about their personal information being exposed at any given time, thinking, "do I own my data input if entered" and potential concerns in the privacy and security features platforms use with procedures in place."
How we use the Internet can affect people's feelings about their online experience. Whether it be through security measures, respecting privacy, or avoiding fraud - there are many things we take for granted when using our smart devices today that weren't always around. But all too often, we don't think twice about the things happening behind the scenes on our devices. This is mainly due to their technological advancement but also because most people never question how these smart gadgets work until later down the road.
What makes up good/safe usage of the Internet?
Is it more about user experience or how tech developers deploy technology?
Keeping internet interactions safe and sound is first to understand what is needed for both user experience and systems (need) to achieve, and how trust is developing, the online presence of DATA and personal information on a particular platform.
The developments of both Metaverse and Web 3.0 are starting to define a Trustless Future. But how close are we to reaching a trustless web experience?
With blockchain at its core, the next-generation internet is where individuals, companies, and governments have more control over their data than ever before. And although many might be doubtful about this, individuals, privacy professionals, established technological leaders, and government officials, we’re openly seeking opinions and feedback.
A realistic view and understanding are that improvements in the utility of Web3 are still a few years away, even a decade, and the Metaverse even lengthier to fully explore. But the question to think about is how far is a trustless technological future, and if it is even possible, 10-20 years?
Please take some careful time to read below how we envision the future of a Web of Sharing Trust-responsibility.
We can expect a more moderately diverse - new online experience in the future where the two primary ways we'll interact; are the conventional online space similar to today's and virtually on the Metaverse. These interesting technologies are mainly cryptocurrency, blockchain, AI and a combination of Internet of things (IoT), XR Extended Reality combined AR/VR or individual use cases in mixed modes. As new developments continue, so should everything between trust, safety, and security happen more seamlessly between providers and consumers.
Web3 and the Metaverse are currently defining the first examples and lifestyle experiences, both professionally and recreationally. Today's expectations are an increase in the market trend forming a decentralized and more trustless technology where we can make easier online decisions.
Web3 is the third generation of the World Wide Web and promises to be the most transformative yet. Whereas Web1 was about connecting people and Web2 additionally was about connecting data, Web3 is about connecting technologies and new user experiences. The third-generation internet configuration will connect people, data and devices and require new standards, protocols and policies to make this possible. A necessary step is how we’ll work jointly to create these measures, to ensure that Web3 will be a force for good in the world. For the first time, the goal is to connect directly without relying on intermediaries. This will open up a world of possibilities for innovation and creativity. Web3 standards, configurations and a suite of innovative tools/protocols will be essential in making this vision a reality.
Responsibility towards trust.
The Web platforms of tomorrow will demand more forms of equal responsibility, as will Internet users, who seek trust and greater practicality. Increasing new web experiences will be more and more defined by developments and improvements in technology and law regulations. The first prospects of developing a trustless ecosystem are to help reduce concerns around trust in privacy and data security. And this is only if confidence is found, and when we recognize where trust continues, that can create and duplicate more trusting knowledge. Today's reality is that we need to build on top of what we currently have and steadily revise for more trusting features that generate a more prominent trustless web ecosystem.
Taking steps toward a trustless ecosystem starts with regulation where trust is prepared and how trusting is tested by associations to co-occur for a "trustless platform" that can drive the ecosystem to thrive.
The trend we've achieved is reaching a vital phase, "the converging bottleneck," – what every other government and private enterprise is looking to gain further. With the emergence of AI technologies, blockchain, and quantum computing, these fields show exciting utility. And industry believes these technologies will engineer better new, and safer solutions for increasing inclusivity and safety for everyone's needs.
Creating leading-edge technologies requires governance and guidance of the frontiers leading industries and vice versa at any time of necessity. Regulation is more than implementing a new set of rules and laws to follow but is also a guide to reaching a destination with crucial objectives:
By what means (with technological advancements and standards changes) do today's reforms assess proposed policies and their defining impact?
What procedures are used for redefining standards and the principles that define algorithms used to manage more evident systematic practices related to rising consumer needs with emerging technologies?
In a world where consumers may get inundated with choices and information about products, developers compete and take off an opportunity with a solution, knowingly or not, which may not necessarily have good outcomes. It is becoming more vital than ever for tech providers and policymakers to find ways to collectively build more trust and objectives for consumers. Simplicity in today's world is never enough, and discovering a point to start developing new values appears like more and more work is needed.
Does this mean reforms and following new additional regulations and standards in favour?
As the pace of regulation change grows, non-compliance actions face reputational risks, and managing compliance risks faster and more efficiently must also make proper guidance for enterprises. Al and automation will bring change and should bring new working, seamless technologies in more secure ways.
But when can we expect this to take shape and take effect?
Unfortunately, today's policies and administrative laws lack the speed to execute, as technologies speed up developments and deployments faster than ever before.
This is a problem; the policy is here, but how to administrate it?
As mentioned, the first question to Australia's 7 RIS questions for policymaking is: What problem are you trying to solve? "RIS requires an explanation of the problem and objectivity – simply and clearly. A crisply defined problem offers scope for innovative, non-regulatory thinking".
The first aspect of developing trust with technology is where transparency demonstrates the use and explainable capacity. With today's ongoing modernizations, every enterprise develops a reputation and character.
The PoD ecosystem below characterizes - the processing, reporting and performance of policymaking and compliance developments that lead consumers to how developers comply with regulation protocols top to bottom and vice versa and what to achieve. This approach performs a "simple structure" of enterprise System-Maturity-Levels (SML), how it serves and understanding of how safe it is, and it's known how a matter of the "specific policy" use is benefiting. Using AI and Automated Decision-Making, ADM can further process a policy in motion to support increasing secure methods that add to the user experience, most importantly, while also encouraging growth, compliance and fair competition for the industry and the economy.
Automated decision-making ADM and AI regulation - is not positioned as a central body, but as a multi-level, and more defined, internal, and external model. We envision this may present fewer conflicts and a suitable way with policy proposals and deployment correctly – for direction when changeovers occur and managing disruption shifts for parties involved, developers, consumers, and policymakers. We have further identified examples below of what we suggest by these statements.
As we have seen so far and imagine the future, the online world is continually transforming and planning for the next evolving technology. Keeping up with the new developments and tech benefits can also be difficult to correlate with privacy laws and regulatory requirements. How the technology provides and manages data input and information now should produce output responses that enable more concise support for future emerging developments more relatable.
We envision that developers and policymakers will eventually interchange seamlessly a direction of any improvable development in general with new and modern products, which should be a good influence. Establishing a pre-deploy policy mechanism model lies with open-source or crowdsourcing “what it’s we value” that eventually can create stronger relationships and trust. The question many expect is how do we allow interoperability with other nations? Establishing expert leaders in key positions is nothing more and only can be improved. Using AI and ADM has helped in only a select few areas. Implementing further advances needs appropriate approaches to be made and managed while ensuring no harm and fewer negative impacts performed.
But how is trust created in an era of constant change and at times of uncertainty, primarily when technology may not always operate as it should?
One way to do this is to focus on creating visibility and display of secure process engaging technologies and regulation models that build results and reputation. Regulation ensures that all interacting parties are prototypical to handling information and data and transparency with who regulates and validates processing. The challenges we are presented with now and future are to create more knowledge and understandable use-cases that lead to growing trustworthiness. Governments and private enterprises can further enhance platform security and safety improvements through participation and practices that will assist to maintain confidence to build on trust. Achieving this is by affirming an overview of how policy and compliance work with track records. Forming a policy that represents secure platform use and user base data needs a straightforward interpretation presenting how it's delivered an adequate understanding and viewpoints of current or new proposed policy.
According to the ICAC Trust and Democracy in Australia report, there is "compelling evidence of an increasing trust divide between government and citizen reflected in the decline of democratic satisfaction".
What is the solution now?
First of all, if there is difficulty administering a policy for enterprises to comply, we point out below how citizens/consumers can help and how policymakers need to look for ways to assist and educate citizens/consumers more clearly about evolving technologies. Additionally, the top priority is the security of data procedures used and how swift the resolve of conflicting issues and risks encountered of any sort. The key to the solution is how to proportionately extend a collaboration model and showcase that transparency and accountability measures - are controlled. And in what manner to enact reports founding parties introduce.
How are reforming policies and regulations with advancing technologies evolving?
Online interactions generate data; [Input-Action-Result]. With the increasing applications in technological advancements, administrative law may have more enhancing effects with more distinct conditions and pre-conditions on how online: input-action-result - specified in the Consumer data rights (CDR) and privacy law. After many years of development, recommendations, policy proposals, drafts, and amendments, it has become inherently difficult with the yet defined data types with protections to (specific) industries and sectors. Amending policies requires measurements that coincide with consumer experience (CX) and user-friendly emerging technologies. Online output is key to defined data type, whilst providing appropriate protections and applicable extensions for participation use, exchange, storing, or transfer of digital data.
Policies and technologies are constantly changing, and markets are always responding to these changes. Some policy changes significantly impact markets, while others might not have as much of an effect. It's essential to develop ways for developers to stay up-to-date on all the latest policy change advances, so there are informed developer-investment decisions.
• What policies or technologies are currently driving market trends?
• What do recent market trends suggest about how markets respond to current policies and technologies?
• What new policies or technologies are likely to impact markets in the future?
• What policy or technology changes are likely to have the most significant impact on markets in the future?
• What are the risks and opportunities associated with policy and technology changes in the market?
Layer 1 Engagements
Introducing: Policy of Developments - Access PoD ™
Policy development and deployment will require technological execution of input, on-demand, with specific metrics, results and standards. Designing and applying new regulation proposals may further be improved with more advancements towards and more adoption of AI-powered policy Simulations, machine learning ML, computer vision CV, and Deep learning DL technologies.
As technology has shown on occasions, there is certain leeway between laws and enforcing more appropriate protections for consumers as tech companies make gradual progress to adapt. The suggestions of where regulations are going, and where/locations, new regulations are enforced create complex ways for companies to adjust or plan developments on time. The opposite end to this is, that there is little leadership of any tech company other than businesses trying to grow more product lines where possible. The obvious solution is how to encourage government(s), agencies, and private enterprise regulation methods that develop a trustful relationship to design the cause and progression of an ecosystem – by making a distinction between industry advantages and consumer advantages. A Trust Rebuilding Estimate Eco-system is the first phase toward a Web of Sharing Trust-responsibility which can process policy developments based on inputs from real-world data participation to engineer solutions from practices below.
A technological future is not about another version of “opening the box with a ready new product” but includes consumers learning more about a technology and product mechanism through research and experimenting, trial/testing, and simulating product offers or policy impacts, which aids to define markets by what tech enterprises/platforms approach.
Layer 2 Engagements
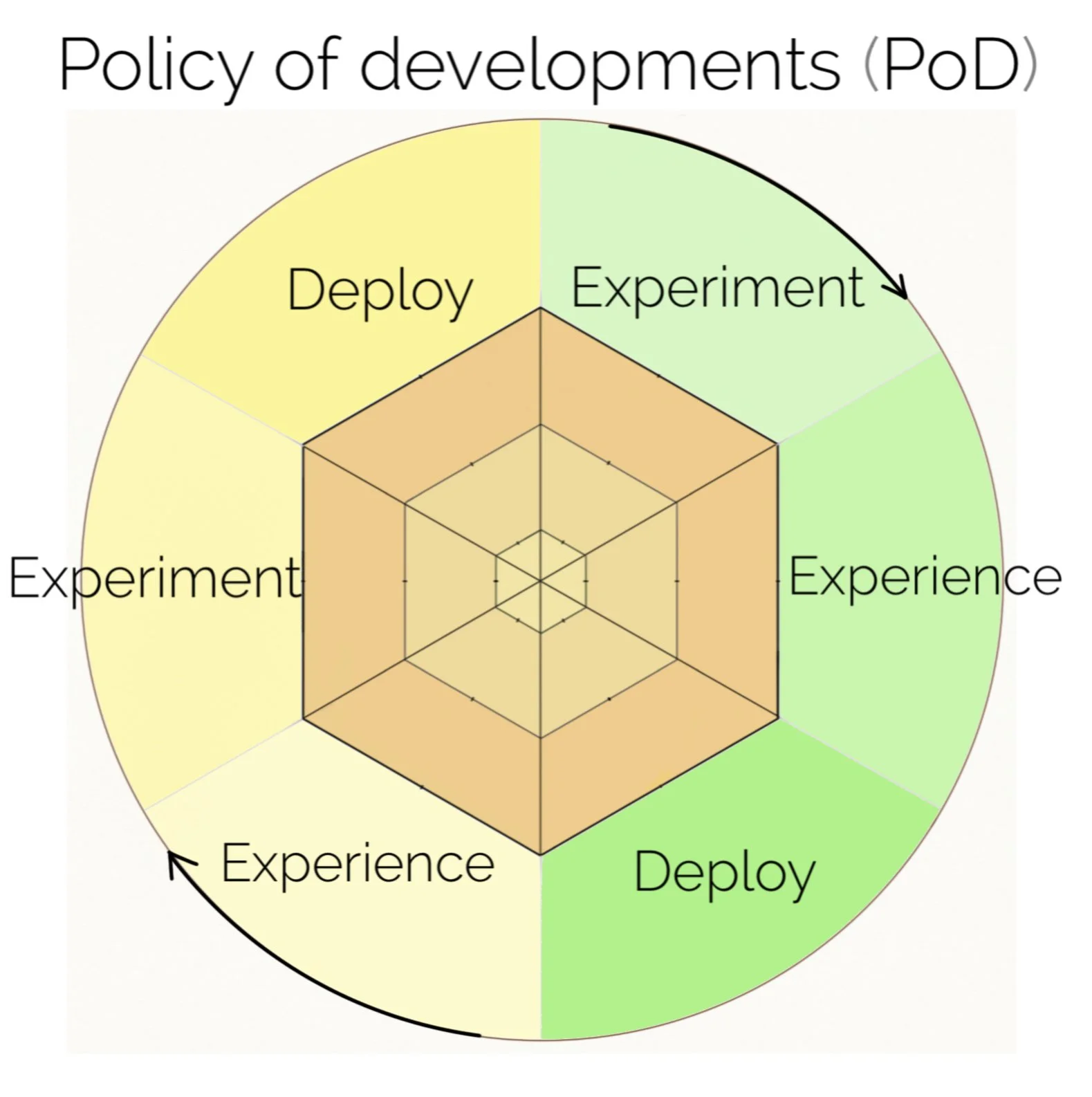
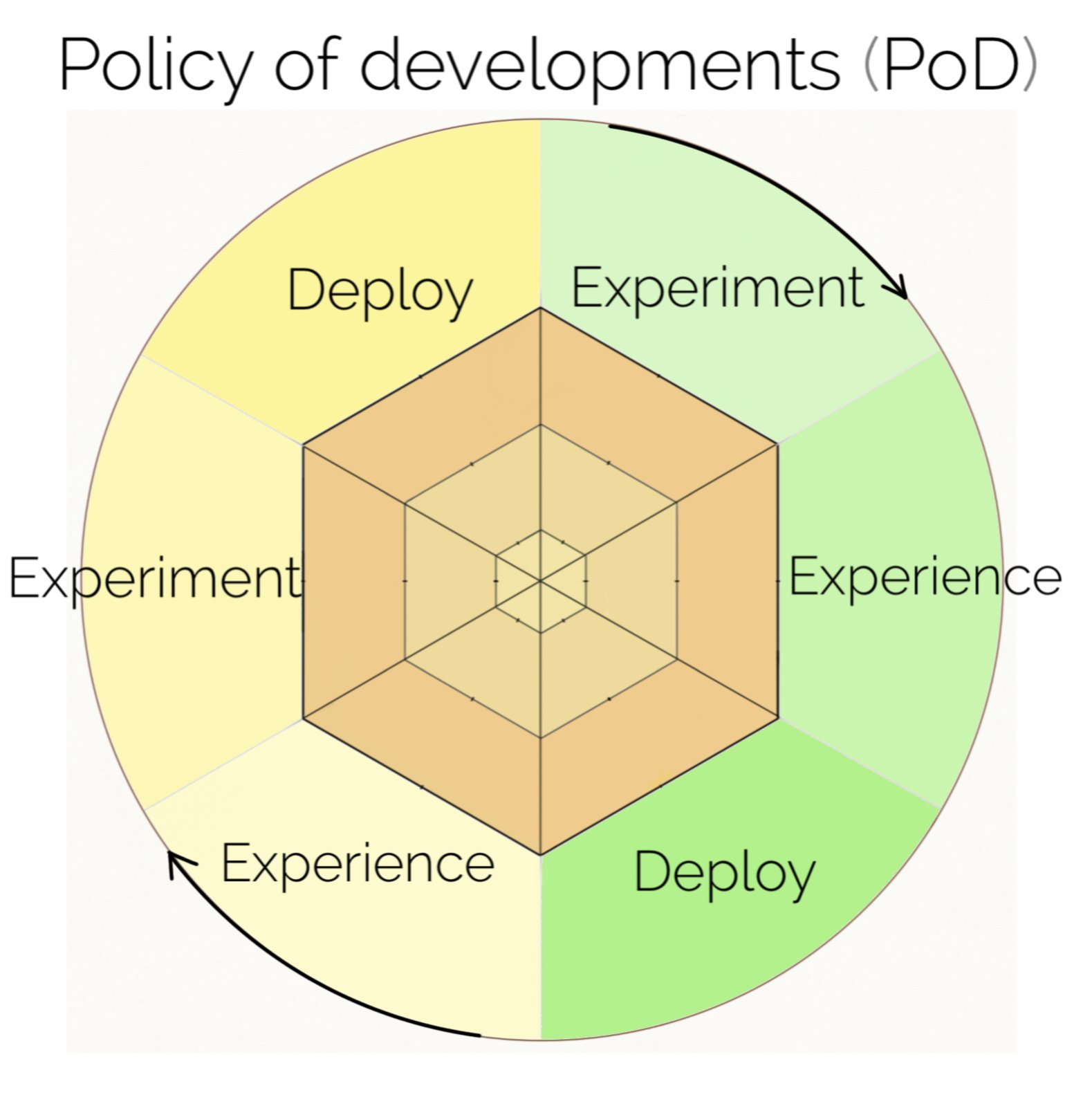
What following methods and metrics are needed for a new pre-deploy approach to policy developments and implementing regulations required before deployment:
experiment, experience, and deployment, is studying risk-taking or launching a:
experience, experiment, and deployment – risk management model?
It is difficult to predict how any existing policy or new proposals (as with this example also) for policy development unfold and what results take shape throughout a policy life cycle or show benefits from commencement other than enforcing and restricting harmful procedures. Developing more areas for policy simulations and estimates around restricting harmful progress and overseeing technology development with proposed policies – Simulation AI-powered Policies (SAPP) may be more viable to develop earlier than later. With approval of random selection of anonymous real-world data and participation with tech providers, government agencies, including universities, our objective is to deliver a comprehensive and systematic study to provide insights about proposed and existing policies with an analysis of:
experiment, experience, and deployment.
Questions we may think about:
Does administrative law enforce the participation of tech providers participating in SAPP or is this voluntary?
When might this be necessary and if at all needed for an industry?
Do Tech providers lead by seeking data from consumers and what approach is necessary to ask for data logs and information needed?
Tech providers who commence with early participation in SAPP developments may offer a trust(ing) consumer-based involvement and means to develop brand awareness. New data is information power when it shows that platforms and policies work based on pre-evaluation and participation methods.
Layer 3 Engagements
Pre-deploy Policy PoD - Second phase toward a Web of Sharing Trust-responsibility
Below is a characterised method, metric-result-format on prior data gathered for - experience, experiment, and policy deployment.
This AI PoD engine delegates administrative policies through an internal and external model, which is processed and measured through our human-centric approach - 6 operational factors. (detailed below) This also sets a limit for proportionate delivery of input and guidance to enact accountability measures between internal and external parties with analysis and performances of:
Experience, experiment, deployment - policy compliances. Risk management.
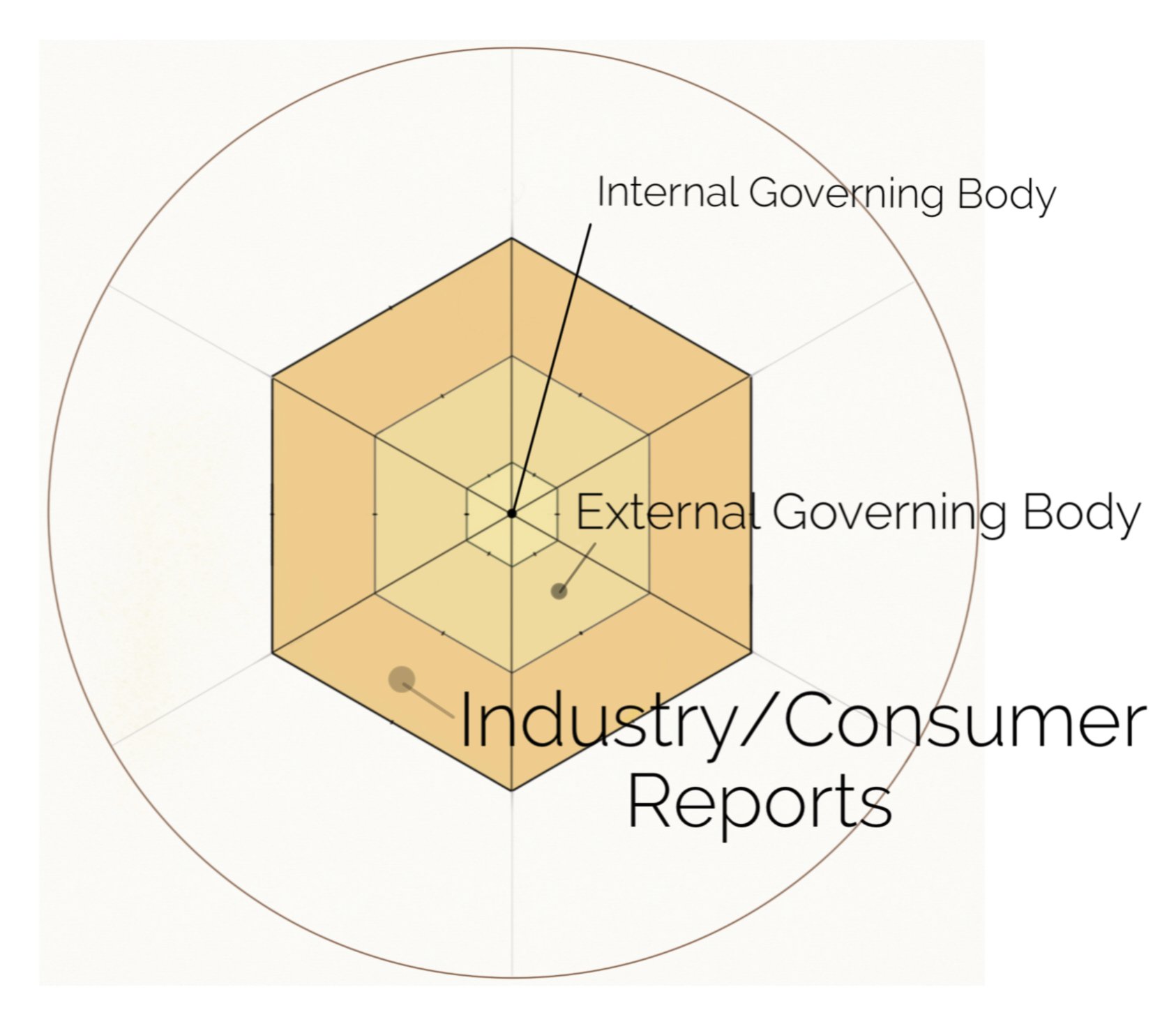
Internal & External Supervision PoD
Internal PoD Department - Delivers the experiential directions of developments studying performances, metrics findings and impact statements. Internal regulation primarily consists of:
1. Government policymakers.
2. Government agencies
Both Internal and External PoD departments participate and review reports either simulated or deployed, managing real-world data and beta/trial testing at known locations. Consumers who choose are encouraged also to provide feedback reviews of proposed policies while tech providers include a pre-start to platform functions, PoD Certificate, and options from features with new policy handling, visual infographic and description updates to policy change.
External PoD department primarily consists of regulation compliance measures, management, and administrative legal practices of:
1. Telecommunication and internet providers.
2. Mobile, tech gadgets, and computing devices.
3. Tech software providers.
The external governing parties co-operate with government internal agencies registered external party providers.
Layer 4 Engagements
Machine Learning PoD
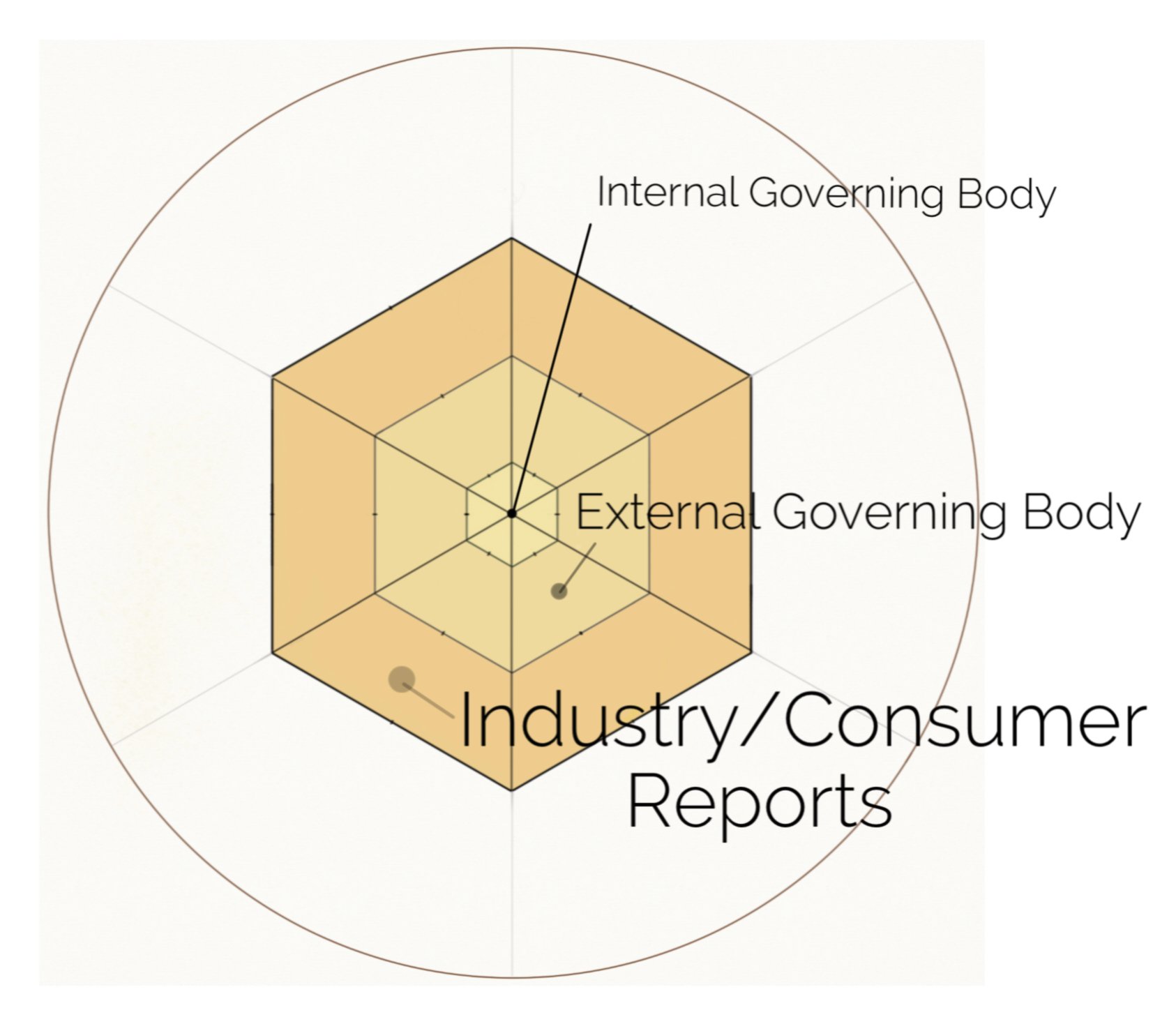
Internal Governing Body
Validating internal policies & Validating external practices.
External governing body
Validating policy & Validating legal practices
6.1 - Industry 4.0 & Security – Secure procedure and processing of data and history and/or if damage/harm is made to personal or ID information, digital information, and data from fraudulent activities, and security steps/protocols taken before personal misuse of data and information. Trust factor
Industry & Consumer Reports
Layer 5 engagements
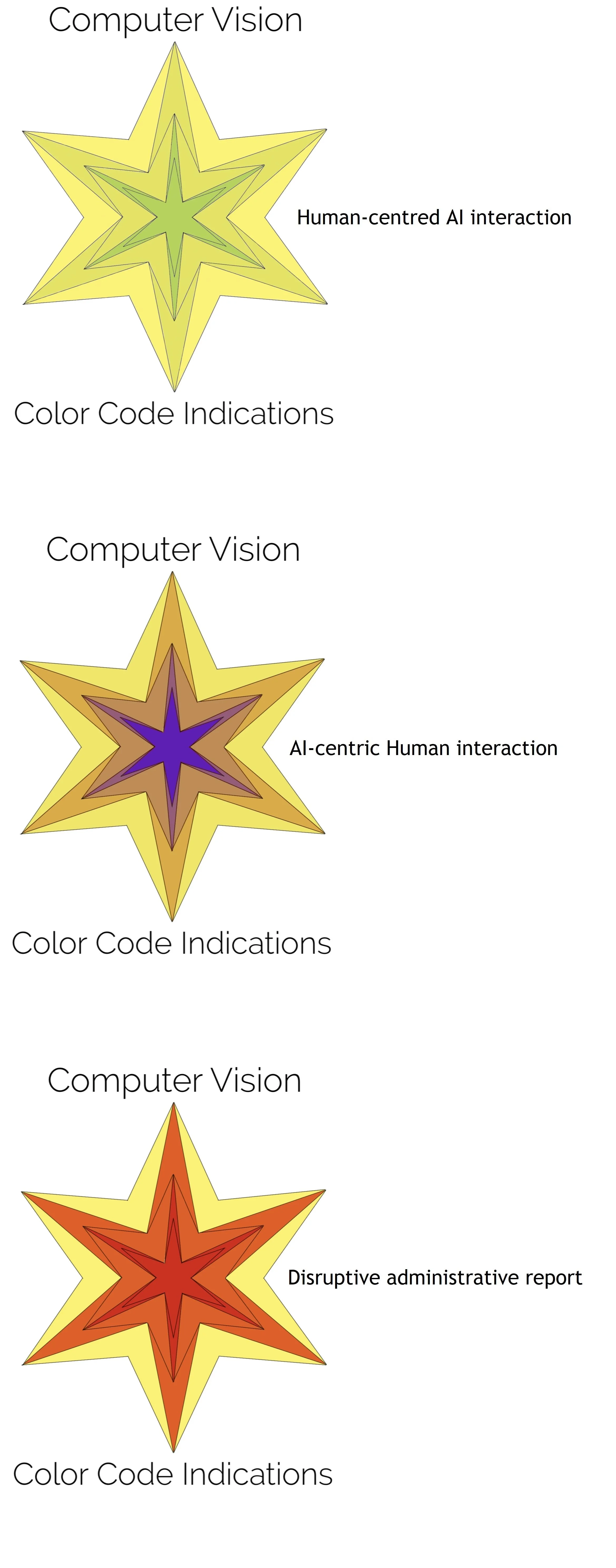
Computer Vision PoD
Defining Policy of Developments - enterprise human-centric path
Layer 6 engagements
Deep Learning PoD
Star PoD indicators and deep learning analysis of Policy of Developments (PoD) weekly, monthly, and yearly reports.
Internal departments and external parties, including independent 3rd party, data inputs, simulations and review, review of real-world policies, and mapping data in real-time.
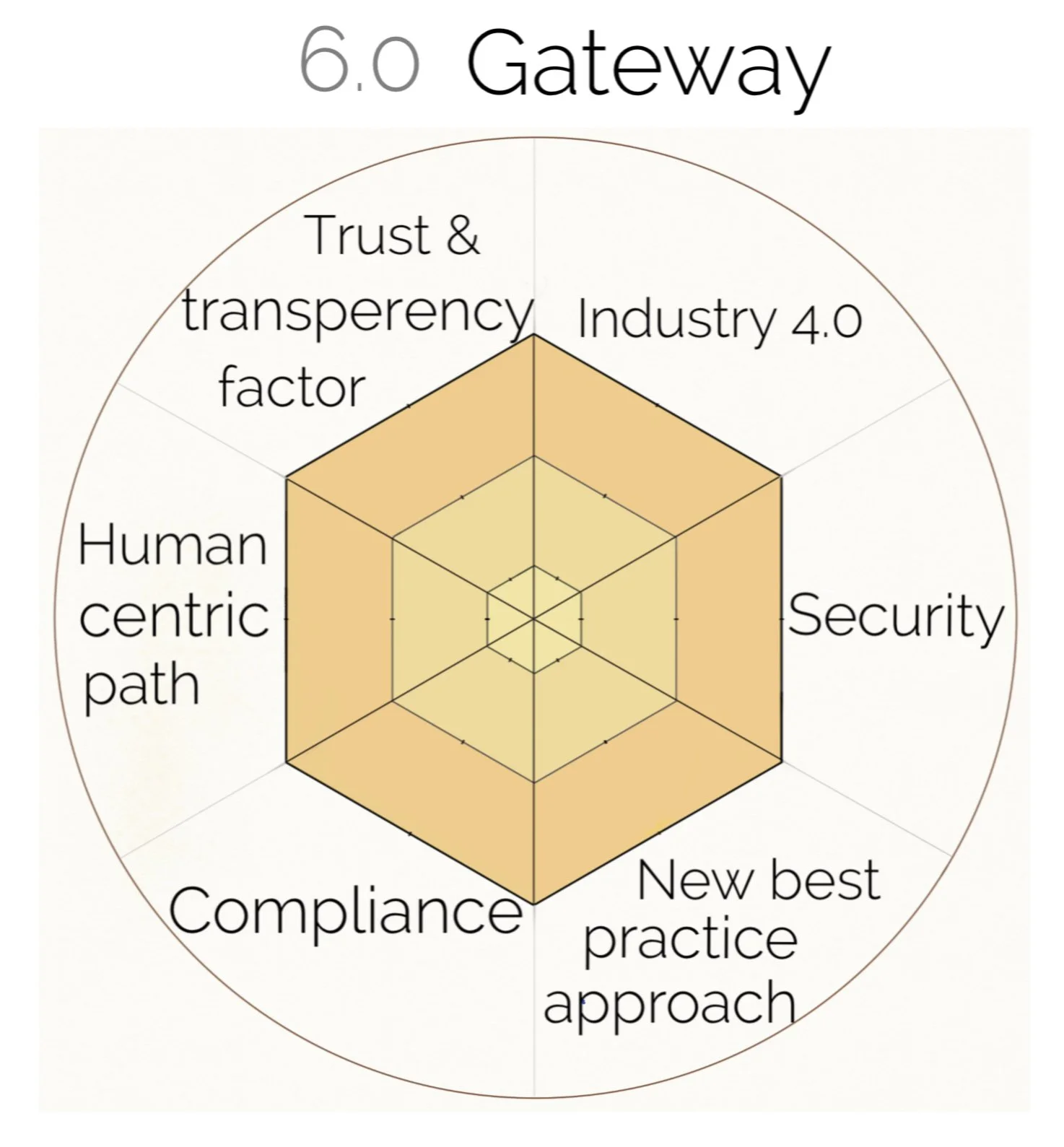
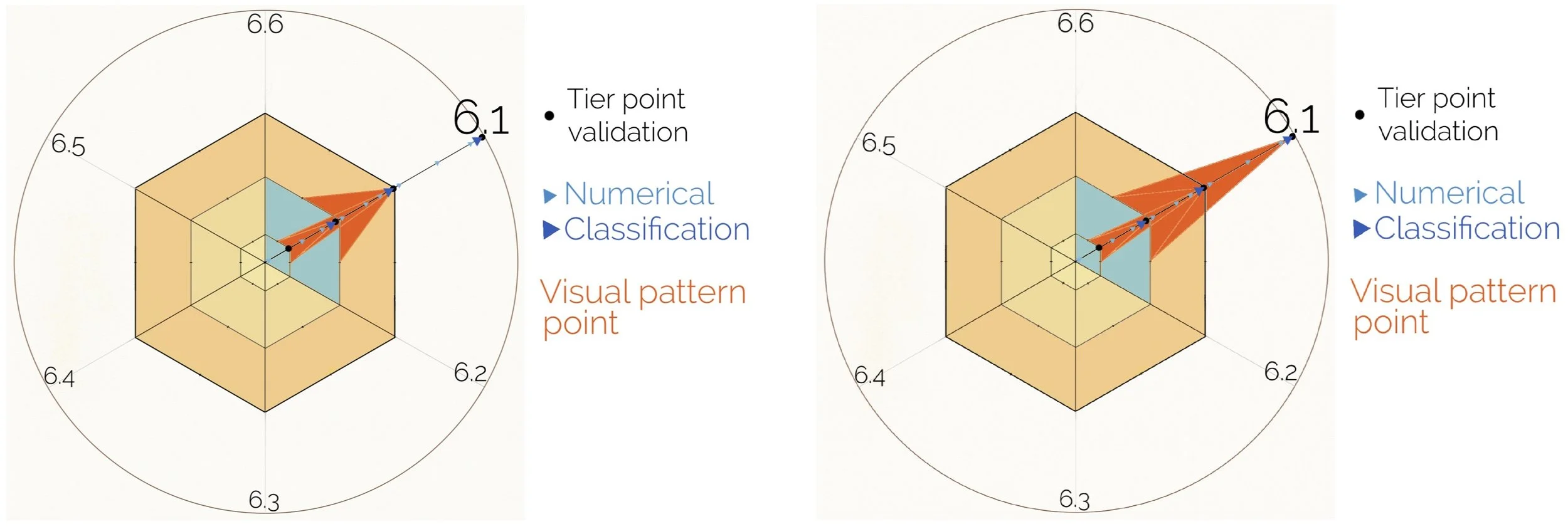
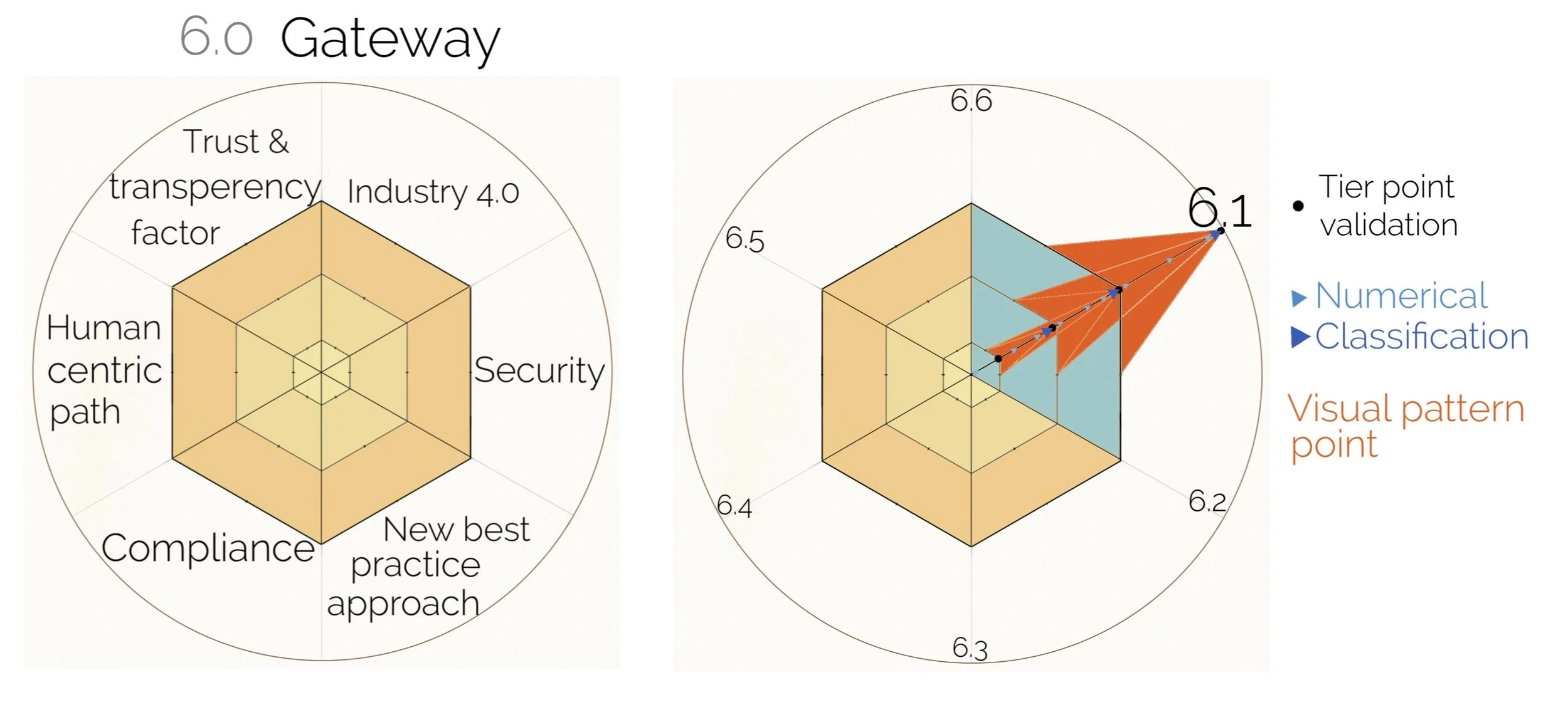
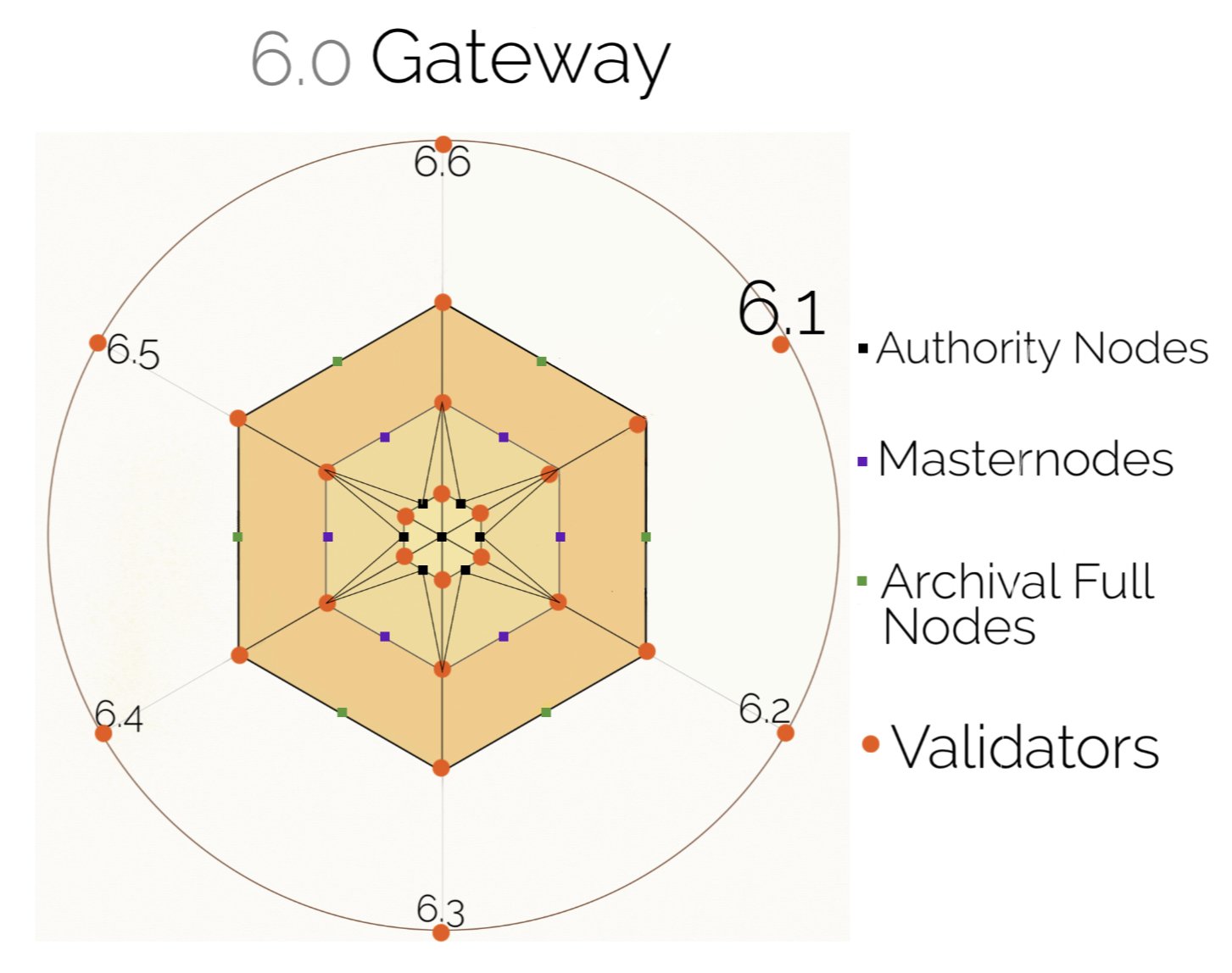
A visual infographic Compliance Star Certificate (CSC) - contains 6 operational factors for managing information DATA reporting about a policy impact:
6.0 Gateway
6.1 - Industry 4.0 & Security – Secure procedure and processing of data and history and/or if damage/harm is made to personal or ID information, digital information, and data from fraudulent activities, and security steps/protocols taken before personal misuse of data and information. Trust factor
6.2 - Security & new best practice approach - When an enterprise augments security protocols and data reports collected of real-world DATA; used, sold, reused, or can be used again with existing policy - trust factor.
6.3 - New best practice approach & Compliance - When industry enterprises adopt a policy and time factor to adaption to change and date adoption of new policy use case, locations used and tested and deployed - Transparency.
6.4 - Compliance & Human-centric path – Compliance measures and legal practices with processing and management procedures and mitigating risk of 6 operational factors - Transparency
6.5 - Human-centric path & trust-transparency factor – Certificates and compliance - observing and measuring results from enterprise offerings and effectiveness in consumer use reports - Openness
6.6 - Trust, transparency factor & Industry 4.0 – How platforms compete and offer a fairer competitive environment (fair competition), and how is intellectual property or opensource tech leveraged and deployed. (This is a critical area on how regulation can be optimized to provide more effective user-friendly tech. How products and services compete is with a level of trust; including brand reputation, due diligence with a human-centric path, spam filter mechanisms, and IP registration credentials issued.) - Openness
The 6.0 gateway establishes compliance developments, including improving online security and brand awareness, accountability measures, and evaluating and comparing standards and ratings within industry, sectors, and enterprises.
Governing administrative framework and legal practices using deep Learning technologies.
Trust is confidence found. As more confidence in technologies grows, more practical consumer growth satisfaction will come from preferences. Much focus is on big tech companies and how they operate, manage, and look after userbase data. This constant conception that big tech must comply with is notable and needs focus as big platforms hold a large user base, and breaches of regulations and other harms occur. However, not overlooking any area, the most significant adverse impacts that occur on an individual level are with unknown online entities that copy/imitate other known enterprises, even cloning whole platforms. This is where the most significant damage can be done to enterprises and individuals, losing digital credentials, data, and misuse of personal information in fraudulent ways.
An internal governing body would seek developments to establish a collaboration model for accredited 3rd party Outside AI Policy (OAP) branches for “AI and ADM advancing levels”. This division Investigates leads and collaborates with branches, patrolling online activities for known and unknown entities, enterprises, or company web browsers for appropriate credentials, certificates, etc.
An Inside AI Policy (IAP) division functions within Internal supervision PoD and accredited 3rd parties for planning, analysis, research, demonstration, and evaluation purposes. Enterprises seek registration and 12 months trial acceptance period overview of compliance and security achievements and notify new adaptions of policy change to enterprises.
Layer 7 engagements
Government agency’s infrastructure for departments of service.
Blockchain technology reports and data centre-distribution platform.
Authority Nodes – namely are government agencies and regulatory bodies. Authority Nodes validate all internal gateways that prepare policy compliance structures then validate the masternode.
Data security and storage.
Consumer/enterprise validation security protocol.
As the prominently known practised areas of Automation decision making (ADM) and AI technologies security features, the process and management of unique or personalized information and data of any sort require a spam filter processing method.
Mentioned below are two-phase provisions for securer online exchange and management of information and data.
Developing and utilizing a Safeguard Pivot (authorization or revoke option) & Auto-Mechanism/filter (SPAM-filter procedure), is to Map Alternative Protocol-control (2MAP-control validation) tool for permitting and securing:
consumers’ end-to-end data transfer and,
consumer data procedure processing on platforms.
Providing and facilitating online/cybersecurity functionality - AI or automation of services needs mechanisms to secure access and store data accordingly, from accredited 2MAP-control validator via:
manual authentication process (MAP) is a safeguard pivot (authorization or revoke option) giving manual control to user preference combinations when to use, store, send, or encrypt or decrypt digital information and data. MAP Authentication
automated launch trust (ALT) is an automated mechanism alternative when a systems recognition filter verifies across–matching device, personal data, location, and security information requests via (recorded IP address) MAP location lock from previous log reports and signal notification. ALT Verification to MAP
A top-tier PoD solution protocol would also integrate; How to demonstrate a multi-layer lead-ship model (MLM) for creating and providing both (improving) online access, Web3 and Metaverse regulation developments. The conclusion should enable a single-level approach taken by each governing party to showcase trust(ing) levels and openness on how to enable paths for progressing inclusive innovation and policy ability and the impact. This means enabling a governing party equal participation in a methodical approach on how to measure a user-friendly and defining human-centric path. The key focus to consider on administrative law is what method is used for explainable AI models (CSC certificate example) for demonstrating compliance and achieving high-level online security.
The emerging Web3 ecosystem and Metaverse, which includes artificial intelligence, are largely "under" or "informally" defined.
Nowadays, we define products and services by the utility it provides. But, it forms off either from Under, to Informally, and Over defined. (UIO defined)
System maturity levels of UIO-defined technologies - human-centric approach.
Under-defined: Something new, that sounds, displays and expresses as useful and interesting, but can cause confusion and/or risks might be involved;
Informally defined: There is a general enterprise/consumer uptake in knowledge and expectations, which follow a procedure and protocol - human-centric approach;
Over-defined: There is good expectation (overview) and knowledge and what to expect next.
With all the "technology of potential" these days, these engaging platforms and concepts have been introduced mainly as decentralized and automated platforms representing interesting proposals and utility. And although these new forms of technologies are appealing, they may still be a few years to a decade away from providing the needed adjustments and structure for emerging technologies adoption. How technologies are defined will impact an improving online experience and a more favourable, fair and competitive economy that lead to building the blocks of a future-fit human-centric path. These technologies would need to help with creating more established ethics and codes of conduct, as we envision; a fully decentralized, safe, trusting automation of features/platforms may only one day be possible with the needs of two primary aspects to be contented.
How tech-literate a consumer base is - to how it is increasing a human-centred – future-fit model.
Technologies required are ones advancing foundational goalposts, but at present, there is only a current sense and expectation of these technology goals and concepts to develop the needed ways to identify advantages.
A Web of Sharing Trust-responsibility
Today's interconnected but complex world seeks simplicity. Through technology and advancing AI, how we study "risk-taking" and "risk management" (mitigate) and learn about the border's technology makes can bring the experience to showcase. Realizing the limits and working steadily, not around boundaries, creates more advantages.
Open Collaboration and Use Notice
The designs, frameworks, and information presented here are crowdsourced and open-source contributions, made available in accordance with applicable national and international laws governing open collaboration and intellectual property.
Any collaboration, cooperation, or engagement with governments, public institutions, or state-level bodies is not presumed. Such engagement, where it occurs, must satisfy clearly defined criteria, including:
alignment with applicable legal and jurisdictional requirements;
use of transparent, measurable evaluation mechanisms; and
consideration of reasonable and proportionate impacts under relevant national laws.
The purpose of this initiative is to promote the sharing of stable, consistent, and well-structured practices for policy signaling and governance exploration. It does so through algorithmic methods, classification frameworks, and evaluative models designed to support analysis of policy development impact.
Nothing in this material constitutes an agreement, mandate, or obligation for collaboration with any nation, state, or public authority. All participation remains voluntary, exploratory, and subject to independent review.